Some definitions
ARPANET
ARPANET short for Advanced Research Projects Agency Network was developed by ARPA of the U.S. Department of Defense in 1968. It was the first step to the actual Internet.
Gateway
Inside a LAN, hosts can talk each other because they are in the same network. The hosts in another network, can be accessed only by a relai , called gateway
A gateway is a host that is connected to two or more physical networks simultaneously and is configured to switch packets between them. It is used to access another network if a gateway is not specified for use. In a network using subnets, the gateway is the router that forwards traffic to a destination outside of the subnet of the transmitting device.
A gateway is the address used for an entry point into another network.
Commonly, the gateway is the address of a network device such as a network router.
It is common to set up the .1 and .2 as a network's gateway.
Example:
If the IP Address is 192.120.10.0, then 192.120.10.1 or 192.120.10.2 could be used as a gateway.
Default Gateway
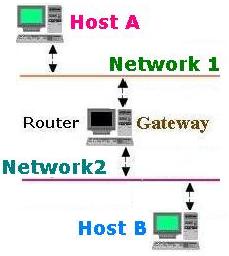
For a node, when sending a packet, if no a specific route is indicated to forward the paket, the first path to follow is the default destination: 0.0.0.0 This temporarily deestination is expected to forward the packet the ultimate destination.
The Host A on Network1 will communicate with the Host B on Network2. The Host A first checks its routing table to see if the Host B is placed in the same Network (Network1), then checks for a specific route to reach the Host B if it exists. If these attempts fail, then the Host A forwards its TCP/IP traffic for Host B to its own default gateway (Router)
The Host B will use the same technique to reach the Host A.
Netmask
A netmask is a 32-bit address used to divide an IP address into subnets.Example:
If the IP Address is 192.120.10.0, the netmask 255.255.255.248 allows us to have 32 sun-networks. Each of these subnets will takes 8 (= 256 - 248) hosts (then : 8 x 32 = 256). More precisely, the number of hosts per subnet is 8 - 2 (256 - 248 - 2); two is subtracted from this number to account for the broadcast and network addresses.
In a netmask, two bits are always automatically assigned. For example, in 255.255.225.0, "0" is the assigned network address; and in 255.255.255.255, "255" is the assigned broadcast address. The 0 and 255 are always assigned and cannot be used.
Broadcast
A broadcast is used to describe a packet sent to all individuals in an area.
Example:
If the IP Address is 192.120.10.0, then 192.120.10.225 is automatically assigned as the broadcast address.
Interface
We talk about interface in networking to mention the machine we use. Interface is the physical port on the ethernet device, where connections to other computers are are made.
IANA
The IP-Addresses are assigned to users by the Internet Assigned Numbers Authority (IANA). They "own" all the addresses, from 0.0.0.0 through 255.255.255.255. They first allocate blocks of addresses to major organizations which in turn allocate blocks to other organizations less large whcih assign blocks to end-users.
LAN
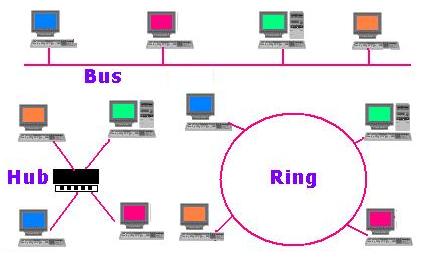
LAN stands for Local area network. It is a network that includes a group of computers in close proximity (&asym; 10km round) to each other such as in a school, a home or an office building. A LAN shares resources like files, printers, and other applications. It connects other LANs, and to the Internet or other WAN (Wide Area Networ).
To build a private network such as a lAN, the related IP-Addresses must be consistent with those reserved and assigned by the IANA.
The reserved IP-Numbers are:
- For a class A Network: 10.0.0.0 ? 10.255.255.255
- For a class B Network: 172.16.0.0 ? 172.31.255.255
- For a class C Network: 192.168.0.0 ? 192.168.255.255
Proxy server
Proxy means acting as a substitute for another. In the networking terms, a proxy server is a software (program) configured usually in the network's user. It plays the role of cahing requests; which is a time saving operation.
Example:
A host "A" requests a certain web page that resides in a certain web server. The related requests goes directly to the web server. Now if a host "B", in the same network as the host "A" (LAN), requests the ame web page, in this case, the Proxy Server will does the job by returning the same web page already fetched for the host "A". By intercepting all the requests, the proxy server forwards them to the web server if they are not already known by it. It is not possible for an external machine todeal directly with a host inside a netwok (disadvantage for a remote connection and advantage for security measure).
NAT
Short for Network Address Translation. With a NAT, the router machine configured on it receives a TCP/IP packet destined for an external machine. It replaces the internals machine IP address with its own IP address and pass it on to the external machine; using only its IP Address for all of the requests from the hosts behind it. The NAT hides many machines behind a single IP address. It gives less security as the proxy server does and it doesn't cahe information.
Firewall
A firewall is a software that assures the same functionnalities than a proxy server or a NAT. Plus the traffic is limited by taking account about the security regarding mainly intrusion viruses and the like. Windows XP (with the Service Pack 2) comes with a software firewall built in (Internet Connection Firewall).
The OSI and its 7 layers
OSI satnds for Open System Interconnection. It is a model that defines a networking framework for implementing protocols in seven layers. Control is passed from one layer to the next. The process starts at the application layer in one station, proceeding to the bottom layer when sending and in the reverse when receiving.
Layer 7:
ApplicationThis layer supports appliacations such as Telnet, FTP, SMTP and DNS. Layer 6:
PresentationThis layer provides transformation of data into the form that the application layer can accept. It also formats and encrypts data to be sent across a networkIt plays the role of syntaxing. Layer 5:
SessionThis layer establishes connections between applications. Layer 4:
TransportThis layer ensures complete data transfer between systems or hosts, and is responsible for end-to-end error recovery and flow control. Layer 3:
NetworkThis layer provides switching, routing, forwarding, addressing, error handling, congestion control and sequencing. It creates logical paths (virtual circuits). Layer 2:
Data LinkThis layer provides encodeding and decodeding packets of data. It gives transmission protocol knowledge and handles errors in the physical layer and flow control. This layer is divided into two sublayers:
- The Media Access Control(MAC) layer which controls how a computer on the network gains access to the data and permission to transmit it; and
- The Logical Link Control (LLC) layer that controls frame synchronization, flow control and error checking.Layer 1:
PhysicalThis layer conveys the stream of an electrical impulse, light or radio signal through the network. It includes hardware means of sending and receiving data such as cables and cards